Pulsara Technical Privacy and Security Summary (US)
Version: 9 | 29 May 2025 | Region: US
Key Points
- Pulsara's Mission: Pulsara is the communications and operations platform that unites distributed teams and fragmented technologies as incidents evolve.
- Pulsara's Purpose: To improve the lives of people in need and those who serve them.
- Secure mobile applications: no PHI stored on the device.
- Secure cloud platform: built on top of AWS, following best practices for the entire application development lifecycle.
- Light footprint on IT: no servers or on-premise hardware to install, and we do all the upgrades and maintenance.
- The platform is secure: security at every level, 3rd party audits, background checks, etc.
- The platform is reliable and scalable: geographic redundancy, horizontally scalable, vertically scalable.
Product Demo Videos
If you’ve never seen Pulsara in action before, please check out our demo videos:
STEMI Demo
Stroke Demo
General Patient Demo
Architecture
- Native iOS and Android applications on, distributed via the Apple iTunes and Google Play app stores.
- Pulsara Web application available on modern web browsers.
- Pulsara MANAGER web application,
- used for administrative configuration, provisioning, and reporting on modern web browsers.
- Platform and APIs run on Amazon Web Services (AWS) infrastructure.
- Access over HTTPS for API and data storage.
- Pulsara-specific proprietary process allows us to horizontally scale operations for all tenants, which is part of our value proposition to customers.
Corporate & Software Development Practices
- Documented and enforced corporate policies and procedures covering privacy, security, and risk management.
- Ongoing policy and process measurement/management.
- All employees go through background checks and at least annual privacy and security training.
- Secure software development lifecycle with strict change-management processes.
- An annual SOC 2 Type II audit is performed.
PHI
Pulsara implements administrative, physical, and technical safeguards to ensure the security, availability, and integrity of ePHI.
- Providers create and share certain PHI via the Pulsara application including
- First and Last Name, Age, Height, Weight, Chief Complaint, Date of Treatment, Hospital Name, Provider names
- Labs and Vital Signs
- Forms of communication include
- Patient-specific, HIPAA-compliant text messages and notes
- Images
- Live and recorded video
- Audio clips
- What is NOT in the Pulsara application
- The patient’s medical record
- Who owns the information?
- As a SaaS vendor, Pulsara is the shepherd of YOUR Data, for the patients that you serve, your end-users, and the hospitals and EMS agencies that we serve.
- Customer owns Data, defined as
- any and all text, graphics, images, audio content, audiovisual content, data, app usage, other materials, and any other information provided on or entered into the software or made available by healthcare providers through the software including all healthcare related information.
How is PHI protected?
- Mobile device security
- No patient information is permanently stored or cached on mobile devices.
- All communications from the Mobile device to the Pulsara cloud platform are via encrypted HTTPS connections,
- We ensure that data connections are only made to verified Pulsara services using HTTPS certificate pinning to prevent man-in-the-middle attacks.
- Screen capture is prevented on Android, and logged for iOS along with a visible warning.
- Automatically display a secure PIN screen after a configurable period of inactivity.
- User password complexity requirements are enforced following OWASP guidelines.
- Optional - Federated Authentication via an OpenID Connect compatible identity provider.
- Optional - ability to require MDM and/or device level lock.
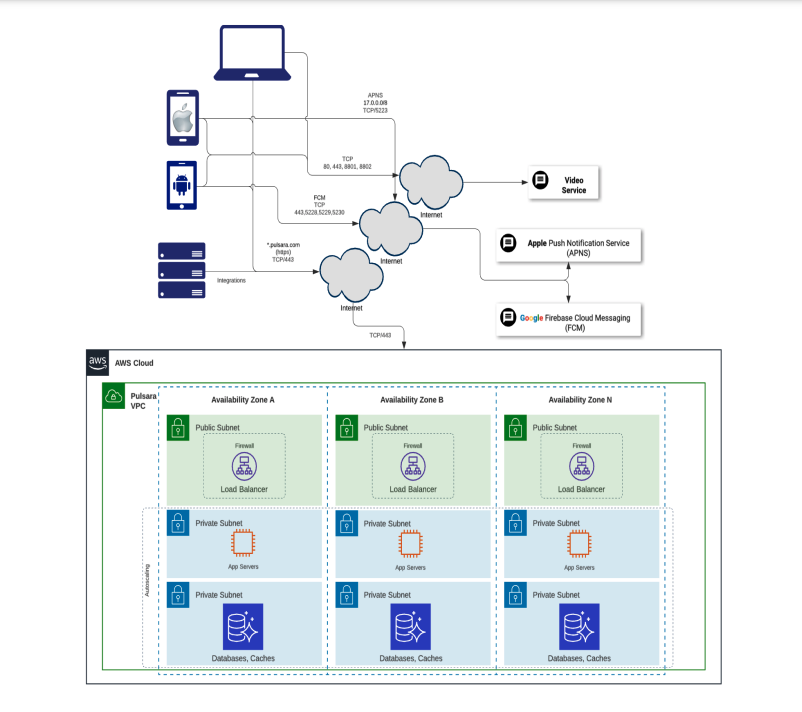
- Cloud and Network Security
- Amazon Virtual Private Cloud hosted in SOC (SAS 70)-compliant data centers within US borders.
- AWS Data centers are staffed 24/7 by trained security guards, and access is authorized strictly on a least-privileged basis.
- See Amazon’s Security, Compliance, and HIPAA documents for more information on the data center / infrastructure.
- Pulsara follows best practices to maintain security of Data, applications, and networks, in addition to the infrastructure level compliance provided by AWS.
- For each container, all services are off, disabled, or blocked by default, and only certain services are added as needed.
- All ports are locked down at the network level by default.
- Up-to-date security patches are deployed with each Pulsara platform release.
- HTTPS is strictly required for all client applications
- HTTP connections are allowed at firewall level but are uniformly redirected to HTTPS at the web-server level.
- Application infrastructure can only be accessed from a Pulsara-owned IP address enforced by: VPN, posture assessment, firewall rules, and using public/private key authentication.
- Pulsara utilizes AWS's serverless environments for Aurora and Container Services as such Pulsara does not manage any servers running in AWS.
- Entire infrastructure is monitored by Amazon GuardDuty that continuously monitors for malicious activity and unauthorized behavior.
- AWS Shield provides Distributed Denial of Service (DDoS) protection for the Pulsara cloud platform.
- Amazon Virtual Private Cloud hosted in SOC (SAS 70)-compliant data centers within US borders.
- Privacy and Encryption
- All PHI and end-user data is always encrypted in transit and at rest.
- Secure HTTPS connection using a minimum of TLS 1.2, SHA 256 with 2048 bit key and a strong cipher suite.
- End-to-end encryption of traffic, using HTTPS for internal communication behind our firewall / load balancers.
- Database backups are encrypted using AES 256.
- AWS managed services for Database and Containers are fully encrypted.
- Role-Based Access Control and Restrictions
- A limited number of Pulsara engineers, based on role, can access production servers.
- Any access to the administration of AWS environments requires that you are on Pulsara Zscaler VPN and coming from a device that passes posture assessment for encryption and anti-virus.
- Disaster Recovery and Data Backup
- Use of multiple Availability Zones with automatic failover allows customers to remain resilient in the face of most failure modes, including natural disasters or system failures.
- Media files are stored in a secure, encrypted S3 bucket and automatically replicated to another AWS geographic region.
- Pulsara utilizes AWS RDS backup. Point in time (to the minute) backups are available for 14 days with daily backups available for 6 months. Pulsara also has a Global replica in a separate region for the US. Daily backups are stored in AWS backup vaults with vault status locked "Compliance Mode" and are immutable. All backups are encrypted to industry standard levels.
- Pulsara maintains a warm, stand-by stack in a separate AWS geographic region where we can transfer production operations in the event of a Production region outage.
Secure Network Architecture Diagram
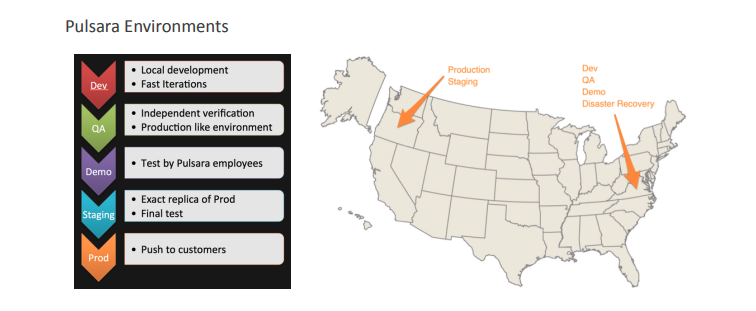
Isolated Environments
- Completely separate, distinct environments for each of the development lifecycle phases.
- Each environment has its own entirely separate virtual private cloud (VPC) with completely independent load-balancer, firewall, NAT, subnets, application tier, database tier, cache tier, etc.
- All environments are provisioned by code, version control, change management, and peer review to ensure consistency between environments.
- PHI data is only stored in the production environment and in data backups of the production environment. PHI is never stored in development or test environments.
- The production environment is in a separate AWS account with extremely limited access.
Scalability & Reliability
Pulsara makes use of AWS Regions and Availability Zones to provide high scalability with automatic addition of compute resources, reliability with automatic failover between AWS Regions if an entire AWS Region goes down.
Horizontal Scale
-
Dynamically increase web tier capacity
-
Distributed asynchronous work queues
-
Clustered database tier with autoscaling of compute, memory, and disk
-
Use of S3 for file storage
.png?width=322&height=272&name=unnamed%20(2).png)
Geographically Redundant
- Compute and data nodes exist in different Availability Zones (data centers)
- Load-balanced with automatic failover
.png?width=512&height=303&name=unnamed%20(3).png)
DNS Failover
- Client applications can always look up Pulsara services
- DDoS protection
- Provided by AWS Route 53
.png?width=260&height=192&name=unnamed%20(4).png)
Shared Security Model